What is double spending in Blockchain and how is it prevented?
Cryptocurrency transactions are safe and reliable thanks to blockchain technology. However, as with most innovative systems, the blockchain has exploitable vulnerabilities, which can lead to double spending. But what is double spending, and how is it prevented?
What is double spending?
Double spending occurs when a single device spends the same cryptocurrency token more than once. This is caused by a flaw in digital currencies that makes them easily reproducible.
The information on the blockchain network can change during transactions, provided certain conditions are met. Once these conditions are met, the altered blocks of transactions can enter the blockchain, allowing the perpetrator to acquire previously used crypto tokens.
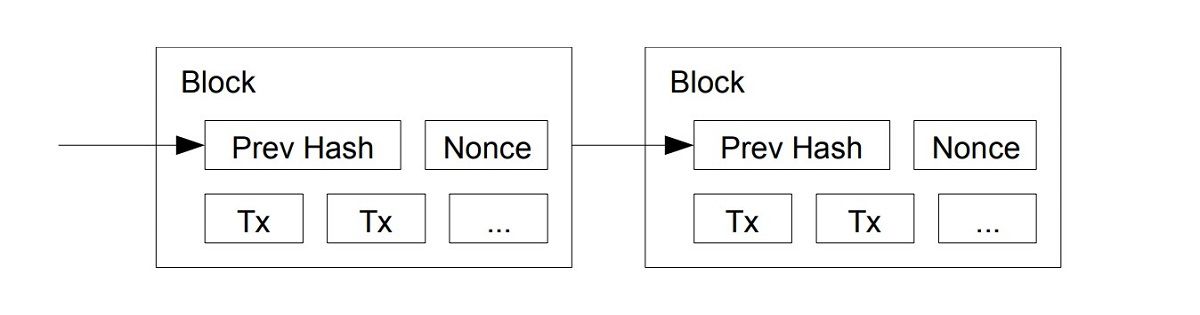
To better understand how this happens, here is a simplified process description. When a transaction is performed on a blockchain network, such as Bitcoin, a block is created that contains the transaction data, the data from the previous block, and a timestamp. The block has an encrypted code called a hash.
The people who mine Bitcoin on the Bitcoin network then verify the transaction via a proof-of-work consensus algorithm, close the block and create a new block. The new block contains the timestamp, the previous block’s hash and the new transaction data. Afterwards, the victorious miner receives block rewards (BTC) for verifying the hash.
To successfully carry out double spending, the perpetrator must mine a secret block that surpasses the creation of the actual block. To do this, the perpetrator must introduce the secret block before the new block, so that the network, tricked into thinking it is the last set of the growing block, adds the fake block to the ever-growing chain. The perpetrator can then claim back the previously used crypto tokens.
Although double spending is a well-known phenomenon in the crypto space, there is no documented case. That’s because verifying transactions is a complex process that requires enormous computational power. Forging or duplicating a block is intense, as perpetrators must work ahead of all other miners on the blockchain.
Why is double spending a problem?
Dual use is an affront to the security of the blockchain network. It happens when there is an exploitable weakness.
Furthermore, the blockchain network must be secure and reliable. If double spending occurs on a cryptocurrency network, it creates distrust in that cryptosystem, deterring investors. And eventually the value of the token will fall.
In addition, double spending is digital theft. The hacker wins while someone else on the network, usually a merchant, loses. The perpetrator retains ownership of the seller’s goods and the crypto token.
Examples of double consumption attacks
There are various forms of dual-use attacks that cybercriminals use. Here are some of them:
51% attack
The 51% attack is the most discussed form of double spending. It occurs when a miner (or a group of miners) controls the majority (more than 50%) of the computing power that validates transactions on the network.
When this happens, they can dictate transactions, create new blocks, reclaim already spent crypto and allocate crypto tokens. It gives them the ability to dual use digital coins.
The 51% attack is less likely to happen in more established cryptocurrencies, such as Bitcoin. This is due to the huge number of miners on the network and the hashing difficulties. However, cryptocurrencies with smaller networks, such as new or forked ones, may be at risk.
In 2014, GHash.io, a mining pool that operated from 2013 to 2016, briefly surpassed 51% of Bitcoin’s computational power on Bitcoin. This development raised significant concerns about the security of the network. Subsequently, Gnash.io voluntarily limited its computing power to 39.99% to restore trust in the network.
Finney attacked
This type of dual use attack was popularized and named after Hal Finney. In a Finney attack, a hacker does not need 51% of the hash power. For it to succeed, a seller must accept an unconfirmed transaction from the hacker, who is a miner.
The hacker generates a block in which he credits crypto tokens to himself by initiating a transaction from address X to address Y (both belonging to him) without broadcasting it to the network. He proceeds to make another payment with the same crypto tokens from address X to address Z, which belongs to a merchant.
If the seller accepts the unverified transactions without confirmation from the blockchain, the hacker releases the block that includes his first transaction. The network invalidates the transaction with the seller after the seller has released goods or services to the hacker. It allows the hacker to do double duty.
Race attack
This attack is easier to pull off than the 51% and Finney attacks. In a race attack, a “race” exists between two transactions.
The hacker uses different machines to send the same token to two merchants. If the seller sends goods or services before the transaction is confirmed, he will discover that the transaction was not accepted during the mining process.
How blockchain prevents double spending
Blockchains ensure against double spending through consensus algorithms, such as:
Proof-of-Work (PoW)
Proof-of-work is a highly competitive process that requires a huge amount of energy. In this consensus mechanism, miners use complex computers to guess the hash of transaction blocks.
A hash is an encrypted, unique 64-digit hexadecimal code each transaction has. This process uses computational power to prove the authenticity of a transaction.
Once the transaction is confirmed, the successful miner adds the transaction to the decentralized digital ledger. At the end of the process, the successful miner receives block rewards in the original digital token.
Bitcoin, Bitcoin Cash, Litecoin, Monero and Dogecoin are popular cryptocurrencies that use this consensus algorithm.
Proof-of-Stake (PoS)
In Proof-of-Stake, participants on the crypto network authenticate block transactions and are called validators. Validators offer (or “stake”) some of their crypto tokens in a smart contract to earn the right to verify transactions before adding them to the growing blockchain.
The network chooses an honest validator based on their stake tokens and stake duration. Once the winner is chosen, it validates the transaction, which the other validators validate.
Just like PoW, validators also receive a reward in the form of income after authenticating new transactions. If the network finds a validator to be dishonest, they lose some or all of their staked tokens as a penalty.
This process is faster and requires less computational power and energy than PoW. Therefore, participants on the blockchain can effectively act as validators.
Ethereum 2.0, Cardano, Tezos and Solana each use their own PoS.
Delegated Proof of Stake (DPoS)
This type of PoS consensus algorithm mandates users on the blockchain to use their digital tokens to vote for honest validators called “delegates”. A delegate is randomly selected to validate new transactions and add them to the blockchain.
After payment, the delegate distributes the block rewards to the users who voted for them.
Cryptocurrencies that use the DPoS algorithm include EOS, Ark, Tron, and Lisk.
No case yet, but dual consumption is a possibility
Although there are no confirmed cases, the emergence of new and forked cryptos and recent technological advances could lead to double spending surprises. Therefore, you should protect yourself by trading on secure cryptocurrency blockchains. And as a rule, wait for miners to confirm transactions before releasing your tokens, goods or services.
.jpg)






