
Trojanized installers for the TOR anonymity browser are being used to target users in Russia and Eastern Europe with clipper malware designed to siphon cryptocurrencies since September 2022.
“Clipboard Injectors […] can be silent for years, showing no network activity or other signs of presence until the fateful day when they replace a crypto wallet address,” said Vitaly Kamluk, director of the global research and analysis team (GReAT) for APAC at Kaspersky.
Another notable aspect of clipper malware is that its malicious functions are not triggered unless the clipboard data meets specific criteria, making it more elusive.
It’s not immediately clear how the installers are distributed, but evidence points to the use of torrent downloads or an unknown third-party source since the Tor Project’s website has been subject to blocks in Russia in recent years.
Regardless of the method used, the installer launches the legitimate executable while also launching the clipper payload designed to monitor the contents of the clipboard.
“If the clipboard contains text, it scans the content with a set of built-in regular expressions,” Kamluk noted. “Should it find a match, it is replaced with a randomly selected address from a hard-coded list.”
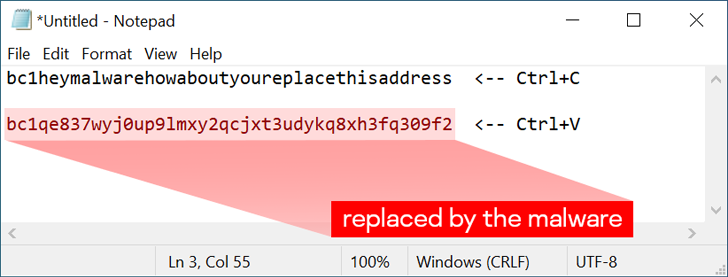
Each sample is packed with thousands of possible replacement addresses chosen at random. It also comes with the ability to disable malware using a special hotkey combination (Ctrl+Alt+F10), an option probably added during the testing phase.
The Russian cybersecurity firm said it recorded approximately 16,000 detections, with a majority recorded in Russia and Ukraine, followed by the United States, Germany, Uzbekistan, Belarus, China, the Netherlands, the United Kingdom and France. In total, the threat has been detected in 52 countries worldwide.
Discover the hidden dangers of third-party SaaS apps
Are you aware of the risks associated with third-party app access to your company’s SaaS apps? Join our webinar to learn about the types of permissions granted and how to minimize your risk.
RESERVE YOUR SEAT
The scheme is estimated to have netted the operators nearly $400.00 in illegal profits through the theft of Bitcoin, Litecoin, Ether and Dogecoin. The amount of Monero assets looted is not known due to the privacy features built into the service.
It is suspected that the campaign may be larger in scope due to the possibility that the threat actors may exploit other software installers and previously unseen delivery methods to target unwary users.
To safeguard against such threats, it is always recommended to only download software from trusted and reliable sources.


