The blockchain network is secured! But not the apps and their integrations
Overview
During the security assessment for a blockchain-based web application, it was observed that some of the functions were vulnerable to unauthenticated ETH transfer from an admin wallet to the attacker’s wallet. The web application was a booking application where a user can book tickets and pay with a crypto token. The application was also integrated with the Metamask framework to support web3 transactions over the blockchain.


Work flow
- User Starts the ticket booking function. Let’s say one ticket (T1) needs a payment of (0.1 ETH) to be transferred to the admin wallet.
- The web application sends the transfer request 0.1 ETH from the integrated Metamask wallet.
- User signs the transaction from Metamask.
- After a successful transaction of 0.1 ETHthe web application confirms the payment with a POST API call to
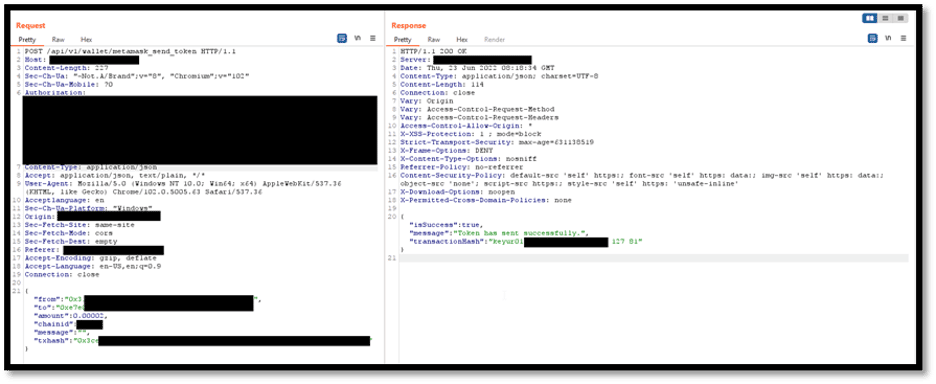
- Now that the application has the successful transaction confirmation from Metamask, the ticket is ordered for the user via a POST request
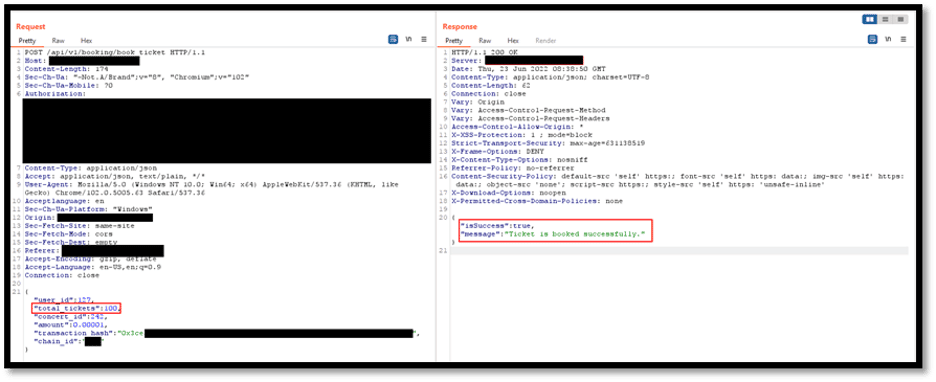
- This POST request is intended for a successful transaction. It contains two parameters viz. transaction hash and total_tickets. It has been identified that these two parameters are not mapped together.
- Since it only checks for transaction hash, the second parameter can be manipulated to order multiple tickets with the same amount.
- A malicious user can tamper with “total_tickets» parameter and can order any number of tickets just for 0.1 ETH. For this given example, we have ordered 100 more tickets 0.1 ETH.
- While further exploiting the vulnerability, it was identified that there was a feature that allows the user to cancel the order and get the corresponding refund.
- When a user cancels the ordered ticket, the backend server only validates whether the ordered ticket is valid or not. After successful verification, the refund is initiated.
- The following functions are performed when accessing this functionality flow:
- get_total_booked_ticket()
- Refund()
- If the user’s wallet contains valid ticket IDs, the underlying server executes a POST request sent to the endpoint: with user ID and “ticket_id” as parameters. The backend server retrieves the ticket’s value from “ticket_id” and sends ETH to the user’s wallet.
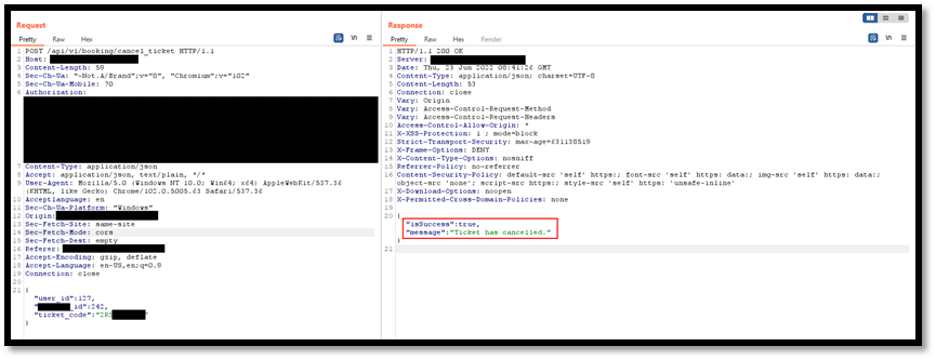
- Any refund/purchase transactions are sent to/from the administrator’s wallet
- Since the API call lacks the correct mapping between the request parameters and does not validate the transactions corresponding to the ticket numbers, a malicious user could easily exploit this flaw to significantly increase the number of tickets and get a refund of more than the amount spent.
- Here, 100+ tickets were ordered for the purchase of 1 ticket which costs 0.1 ETH. By initiating a refund, any amount can be recovered simply by changing the number of tickets.
- As there was a large number of valid tickets in this case, a threat actor can collect up to 10 ETH (100*0.1=10) from admin wallets and empty ETH from admin wallet.
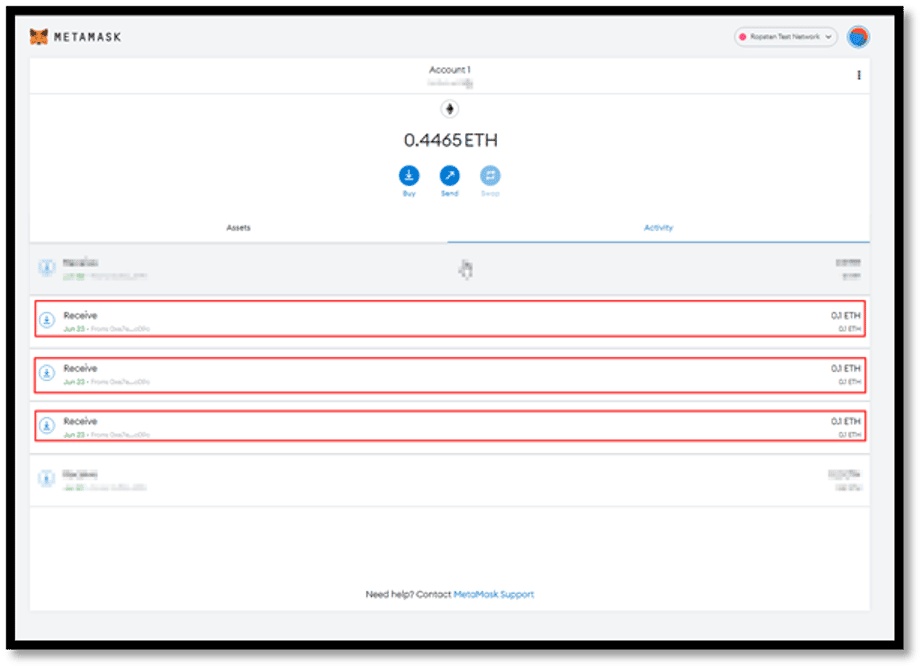
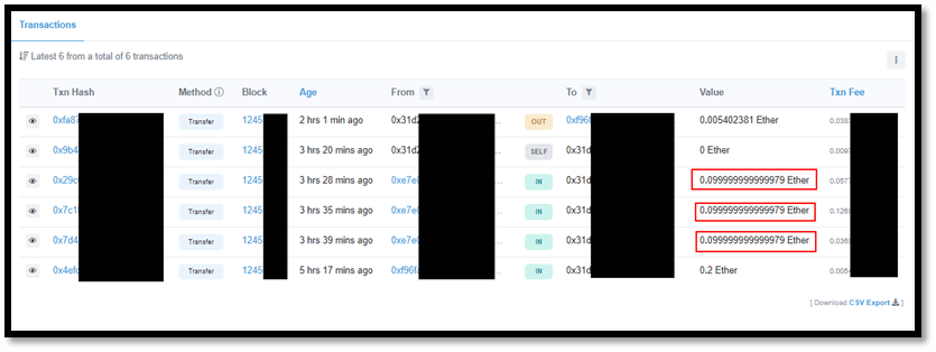
- This payment error was further confirmed by verifying the blockchain hashes from Etherscan (a website that tracks all Ether-based blockchain transactions)
Conclusion
Blockchain network is actually hard to penetrate since Blockchain has the secure network to build DAPPS, but application architecture, source code, workflow and configurations are always open to such attacks. It is necessary to use security audits and regular assessments to discover the vulnerabilities and errors in the workflow. A small problem can lead to unauthenticated token drain from the wallets which will have a bad impact on the users as well as the whole community.
The post Blockchain Network is secured! But not the apps and their integrations appeared first on WeSecureApp :: Simplifying Enterprise Security!.
*** This is a Security Bloggers Network syndicated blog from WeSecureApp :: Simplifying Enterprise Security! written by Keyur Talati. Read the original post at:


