All investment/financial opinions expressed by NFTevening.com are not recommendations.
This article is educational material.
As always, do your own research before making any kind of investment.
all about cryptop referances
A fake Pokemon NFT game appears to be infecting people’s computers with malware. Hackers are trying to use a rogue Pokemon NFT trading card site to conduct phishing attacks on unsuspecting victims. Read on to learn more about how to avoid falling into the trap!
Pokemon has been no stranger to web3 and the wider NFT space. Hackers use a Pokemon game which, once installed, distributes the NetSupport Remote Access Tool (RAT). With this tool, the hackers gain control over the victim’s device. The group is currently disguised as a legitimate Pokémon NFT card game to make money. The website “pokemon [dot] io” is still online.
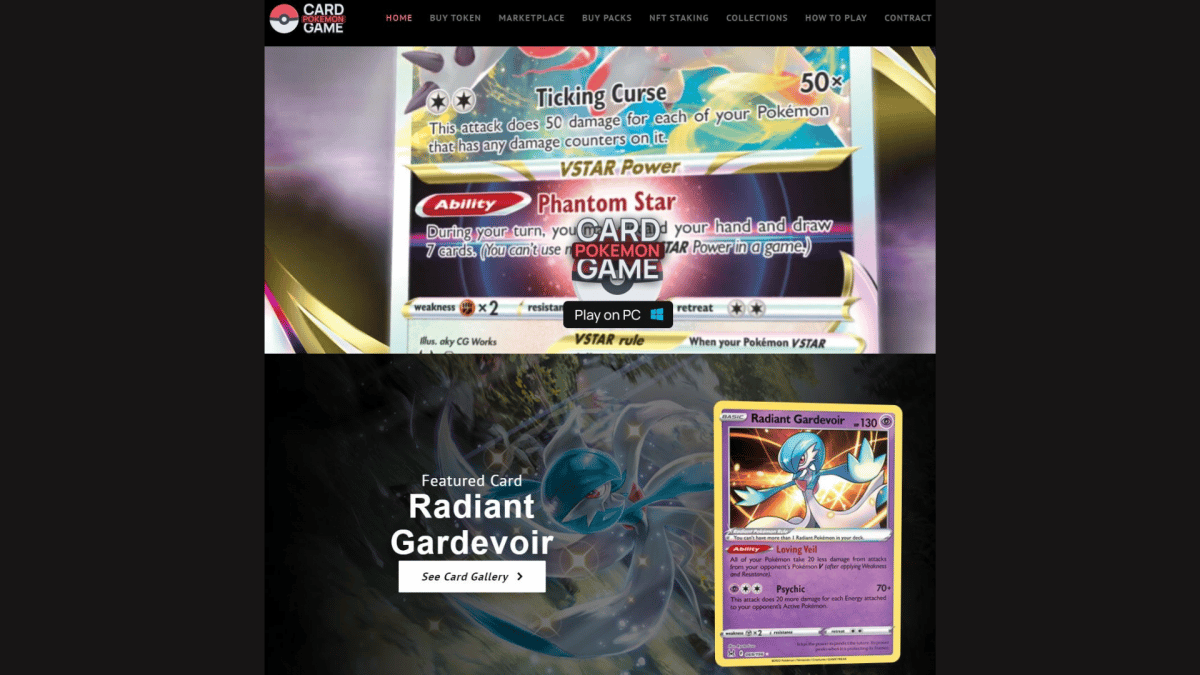
According to a report by BleepingComputer, users who clicked the “Play on PC” button on the website automatically had the installer downloaded. The installer ran unsuspectingly, leading people to believe they had downloaded the game itself. But in reality, the installer implemented the remote access tool on their system, which then allows the hackers to bypass security software on the victims’ systems.
Once installed, the NetSupport tool allows hackers to remotely connect to a user’s device to steal data or install other malware. The NetSupport manager allows remote monitoring of monitors, screen recording, system monitoring, etc. Additionally, this is revealed to be an alternative operation by the hacking team. According to ASEC, there was a second campaign that used the site “beta pokemoncards[.]io,” but this page has been removed.
The amazing popularity of Pokémon makes this marketing campaign an easy sell to unsuspecting fans and collectors of the franchise. ASEC advises people to be wary of the threat group and spread the word among the community to stop the spread of the malicious software attack. NetSupport RAT is a legitimate program that allows system administrators to remotely access devices. For this reason, hackers often use it to evade security software measures. You can read more about this specific attack on the official ASEC statement.
All investment/financial opinions expressed by NFTevening.com are not recommendations.
This article is educational material.
As always, do your own research before making any kind of investment.