Hundreds of Bitcoin Wallets Controlled by Russian Intelligence Agencies Revealed: Report
Important takeaways
- Hackers found a way to tag 986 BTC wallets allegedly linked to Russian state intelligence agencies
- The vigilante gained control of some of the private keys of these wallets and donated these funds to Ukrainian aid organizations
- Three wallets out of 986 have been confirmed to be linked to the Russian Foreign Military Intelligence Agency (GRU) and the Foreign Intelligence Service (SVR)
Share this article
Hackers revealed that 986 unique BTC wallets have allegedly been used by Russian state intelligence groups, in the middle of the complicated relationship between crypto and the Russian government.
A recently deleted Chainalysis report from April 26 revealed that by using the OP_RETURN blockchain feature, which allows senders to attach messages to transactions, Bitcoiners can track the more “aggressive use of BTC” by Russian state intelligence groups. Almost 1,000 wallets were linked to Russia’s Foreign Military Intelligence Agency (GRU), Federal Security Service (FSB) and Foreign Intelligence Service (SVR).
the OP_RETURN function, according to Bitcoin Wiki, allows a user to cancel the transaction and “has at times been used to convey additional information necessary to send transactions“, meaning that burned transactions can also broadcast and keep added messages on the blockchain forever. The so-called “OP_RETURN vigilante” burned over $300,000 in BTC for sending messages via BTC transactions to these addresses between February 14, 2022 and March 14, 2022 – something that started Russia’s invasion of Ukraine in the middle of the informant’s quest.
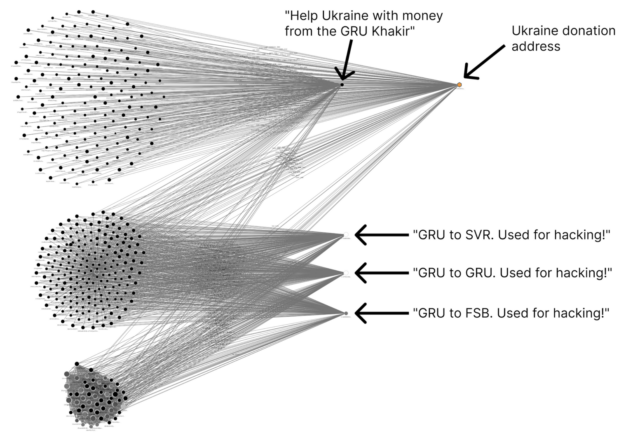
The transactions included the four following texts in Russian:
- “GRU to SVR. Used for hacking!”
- “GRU to GRU. Used for hacking!”
- “GRU to FSB. Used for hacking!”
- “Help Ukraine with money from GRU Khakir”
In addition, the vigilante is suspected of gaining access to the private keys of these wallets marked with the above four messages because the vigilante returned in April 2022 to send money from these wallets to Ukrainian aid addresses.
“The possibility that the OP_RETURN sender obtained private keys for Russian-controlled addresses also suggests that the Putin regime’s crypto operations are not secure,” Chainalysis reported.
At least three of these wallet addresses have been confirmed to be owned by Russian agencies, according to the report. Wallets …ytPm and …2uPf are owned by SVR, cybersecurity firm HYAS confirmed in a now archived post. Wallet …4hDH is owned by the GRU, which was confirmed by the wallet’s connection to DCLeaks.com which had been spreading disinformation about US politicians leading up to the 2016 US presidential election.
While the Russian government agencies have yet to respond to the validity of the above claims, blockchain experts and hackers found a way to estimate how Russia has used crypto to its advantage in the war against Ukraine.
“These OP_RETURN messages will be there forever – no government or company can take them down,” said the Chainalysis report, which highlights how government officials may struggle to understand basic principles of blockchain technology.
Crypto’s relationship with Ukraine and Russia
Ukraine has fully embraced the use of crypto since the start of the war as an easy way for people to donate to the Ukrainian war effort. The Ukrainian government managed to collect $600,000 in donations in a matter of days and over 70 million dollars within weeks of the war, with notable names such as Vitalk Buterin, the Canadian-Russian head of Ethereum, tweeting in support of Ukraine.
Reminder: Ethereum is neutral, but I am not.
— vitalik.eth (@VitalikButerin) 24 February 2022
Across the border, the Russian government has been leery of crypto adoption. In July 2022, Russian President Vladimir Putin included in the law a crypto ban on payment for goods and services. Meanwhile, the Russian Duma expressed interest in develop a digital ruble CBDC for 2023 is only used for specified goods and services.


