Enhancing Energy Conservation Using Blockchain-Enabled Cognitive Wireless Networks for Smart Cities
It is crucial to use the node trust value as an important measure to cooperate in CSS to increase the security of CWN. As a result, integrating the node trust value with the basic system design can improve the sensing accuracy while reducing the energy utilization. To avoid data ambiguity, the blockchain management center can be more efficient20. The proposed flowchart improves the accuracy of sensing and the performance of CWN, so this method begins with estimating the consistency of the system. This estimate is based on available statistical information. When an accused node is identified, it generates an immediate decision to isolate the node’s sense data. The method achieves system elasticity, but increases energy utilization, and the effects of global variations on the node are not taken into account. The licensed user’s living conditions have an impact on node sensing. For example, when the licensed user’s location changes, nodes with strong sensing may become mischievous in the next moment, while nodes with low performance become trusted nodes. As a result, to detect modifications in node status, a real-time node evaluation system must be established. When the efficiency of a node deteriorates, it can stop detecting real-time work, and when it improves, it can be moved to work in real-time.
This paper establishes an interpretation of nodes and an evaluation of the node method to determine and identify nodes more efficiently. Before performing spectrum sensing procedures, the CWN determines the consistency of each node, which is based on scientific data. The original target will continue to work when the global environment is stable, but when the global environment changes, the node’s consistency must be reassessed. To prevent problems, the node’s reliability level is calculated using Eq. (9), and FC creates a node list and transmits node data to the blockchain management center. The Administration Center efficiently delivers node data and is responsible for scheduling nodes to engage in cooperative sensing based on the needs of the Fusion Center.
$$\begin{aligned} y_u = \frac{\sum ^m_{a=1} |L_{u,a}| * l_{u,a}}{\sum ^m_{a=1} |L_{u,a}|} \end{aligned}$$
(9)
\(y_u\) represents the initial confidence value for \(u_{th}\) urge, \(|L_{u,a}|\) means CSS i onecycle of sensing of uurge, \(l_{u,a}\) indicates the value acquired in onecycle of sensing of uurge. When \(l_{u,a} = 1\); means unode i onethe sensing cycle is reliable with FC, and \(l_{u,a} = 0\); means unode i onesensing cycle is not reliable with FC. The evaluation and interpretation of nodes obtained by Eq. (9) is used to store the value in the blockchain management center. The steps for evaluating and interpreting nodes are explained as:
-
First, check if the global environment has been modified, if yes, re-evaluate the trust value of the nodes, otherwise sensing nodes do not need to be changed.
-
The FC will then establish the list of the node’s trust values.
-
Later, the blockchain administration center is responsible for managing and scheduling nodes.
-
Further adjust the number of sensing nodes and then call the nodes whose trust value is greater than the threshold value to engage in CSS.
Efficiency return value ehenergy utilization return value eutotal yield value orefficiency coefficient \(\rho\)correction of energy utilization coefficient ecand total correction coefficient etc are the three return values and three correction coefficients set. These are calculated in the given equation. (10) for the efficiency return value eh:
$$\begin{aligned} is = \frac{1}{m} \sum ^m_{a=1} [(1-\beta _a)(\alpha _a * W_C + (1-\alpha _F)P_C)] + \beta _a(\gamma _a * W_C + (1-\gamma _a) * P_C) \end{aligned}$$
(10)
In the above equation. (10), the value of \(\beta a\) is either 1 or 0 indicating that if 1 means that the licensed user is in sleep mode and 0 indicates that the licensed user is in active mode, u represents the same as given above, \(TOILET\) means the value coefficient and \(P_C\) means the illegal coefficient. In this equation, \(\alpha _a\) and \(\gamma _a\) are the weighted coefficients represented in Eq. (11).
IN \(H_0\) \(\right arrow\) \(\alpha _a\) \(=\) 1, \(\beta _a\) \(=\) 0, \(H_1\) \(\right arrow\) \(\alpha _a\) \(=\) 0, \(\beta _a\) \(=\) 0
$$\begin{aligned} In H_0 \rightarrow \gamma _a = 0, \beta _a = 1 \quad and \quad In H_1 \rightarrow \gamma _a = 1, \beta _a = 1 \end{aligned}$$
(11)
The representation for calculating energy utilization eu is shown in Eq. (12)
$$\begin{aligned} eu = \frac{1}{m} \sum ^m_{a=1} [E_WZ_a + E_P(1-Z_a)] \end{aligned}$$
(12)
where \(YUCK\) represents the value energy utilization which states that the node used for energy utilization is lower than the threshold value; \(E_P\) represents the penalized energy utilization which states that the node used for the energy utilization is higher than the threshold value. \(Z_a\) is the energy return value for the weighted coefficient and the value is given in Eq. (13) as: \(Z_a = 1\), \(\tau _0\), \(\sum ^{I_v}_{a,u}\) = 0
$$\begin{aligned} Z_a = 0, \tau _0 – \sum ^{I_v}_{a,u} < 0 \end{aligned}$$
(1. 3)
where \(\tau _0\) represents the threshold for energy utilization in a sensing duration. Total return value for energy utilization is calculated in Eq. (14) as:
$$\begin{aligned} or = 0.3er + 0.7eu \end{aligned}$$
(14)
This equation describes that 30% of the weight is assigned to the energy utilization return value and the remaining 70% of the weight is assigned to the efficiency return value. Thereby, authors have focused on the sensory efficiency while taking into account the minimization of energy utilization. The equation for calculating the coefficient correction \(\rho\) is:
$$\begin{aligned} \rho _u = \sum _a (\mu _{a,u} – \beta _a) \end{aligned}$$
(15)
The total number of repetitions uthe node communicates incorrect information until FC is represented by the correction coefficient \(\rho _u\); \(\mu _a\),u shows that i onesensing cycle, the result given by unode of the fusion center; \(\beta _a\) reflects the result of onethe sensing cycle’s decision. The correction coefficient for energy utilization is indicated by ec is calculated in the equation. (16).
$$\begin{aligned} ec_u = \sum _a S_{a,u} * J_{a,u} \end{aligned}$$
(16)
The total number of repetitions uth node increases the value of the threshold is represented by the energy utilization; equiv. (17) shows the meaning of \(J_{a,u}\). In case \(J_{a,u} = 1\) funds \(v_{a,u} – \tau _0 >= 0\) and \(J_{a,u} = 0\) funds \(v_{a,u} – \tau _0 < 0\). \(\tau _0\) means that the threshold value is raised for energy utilization and its value is calculated where I is the total number of nodes present in the CWN; and \(v_{a,u}\) tells that the energy used for unode i onesensing cycle is shown in Eq. (17).
$$\begin{aligned} \tau _0 = \frac{\sum ^I_{u=1} v_{a,u}}{I} \end{aligned}$$
(17)
The predefined value for the total correction coefficient oc is shown in Eq. (18).
$$\begin{aligned} oc_u = 0.3\rho _u + 0.7ec_u \end{aligned}$$
(18)
\(oc_u\) is the total correction coefficient for unode which is obtained from the total weighted count of the effective and energy utilization correction coefficient. The efficiency is evaluated with 30% and 70% respectively for the correction coefficient for effective and energy utilization. The trust value of the nodes is calculated as shown in Eq. (19).
$$\begin{aligned} y_u^{r+1} = y_u^r + (\omega oc – (1-\varphi ) oc_u^r) y_u^r \end{aligned}$$
(19)
In the above equation. (19), \(y_u^r\) shows the nodes trust value i onesensing cycle for uurge; \(y_u^{r+1}\) shows the current node’s trust value for \(u_{th}\) urge; \(oc_u^r\) is the total return value of the sensing cycle; the \(\varphi\) specifies the value either 1 or 0. More the value of \(\varphi\) provides better efficiency for energy utilization. The flow chart for evaluation and interpretation of nodes is shown in fig. 4.
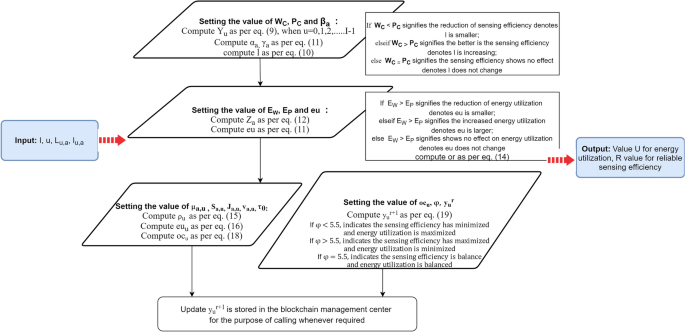
Flow chart for evaluation and interpretation of nodes.
The complexity of the proposed flowchart is O(I!) where O is denoted Big O Notation, I is the total number of nodes in the trust value. In the design flow chart, the main difficulty of blockchain-enabled CWN among the IoT devices shows that this article consists of the blockchain system, CWNs, and IoT devices. FC is where users interact with the blockchain system. The IoT device provides node data to the FC, which searches for node data in the blockchain system. The node then sends verified by the private key to the FC, which validates whether the sensor node has a matching private key pair. If so, send the node’s request to the blockchain system, and the blockchain system’s confirmation to the sensor node. The data verified by the sensor node can confirm the identity of those participating in the CSS and guarantee that their message has not been tampered with. The steps to be followed for designing the CWN are:
-
First, check the sensor nodes in the CWN. It transmits the information to nodes and then requests identification of encryption to FC.
-
Second, examine the verification request of the blockchain administration center.
-
Third, the blockchain management center returns the verification information to the FC and then returns the encrypted data to the sensor nodes of the CWN.


